Okay, so I had the exact same question. (I live in a state where it’s legalized) Being the curious type, I hit up my coworkers to better understand what was going on when it was brought up at a happy hour.
The way my coworkers broke it down was simple: Consider gummies a pill. It’s not a snack, it’s a delivery method…

Data queries and reporting via T-SQL.
They have a pure electric model that is non-US in a model that is slightly smaller than a Renegade. US market for things that small isn’t enough to justify it apparently.
This is a case where it’s using battery packs to help with the demand spikes, not a replacement to power generation.
This is already a practice in the actual power grid. In some areas, large centralized battery banks are used to bank electricity to help ease demand during the spikes. This is just a proposal to shift…
They exist, they just have to be careful how they advertise. Bose has units that pick up ambient, amplify it based on smartphone controlled settings, and play to their ear buds as an example.
Both the prescription ones that exist today, and the gray-area ones that are already on the market support having a bluetooth…
Many already do.
Honestly, this is dangerous advice. It sounds good on the surface, but is terrible in practice.
That’s coming from an IT pro that has deployed LTSC and all of the other versions to global environments. It sucks for home users, normal employee endpoints, and most end up switching to a full OS down the road.
LTSC is…
I would propose that it’s less about the products, and more about the marketing angles in this case.
Nowadays, I use a purpose-made electric insulation blanket over the most exposed pipes. Typically, only the most exposed section needs it, as it warms the pipes just enough to keep it above freezing.
Prior to that, we always solved this by leaving a few faucets trickling. Not the best for water conservation, but I grew…
Best advertising money that dealership has ever spent.
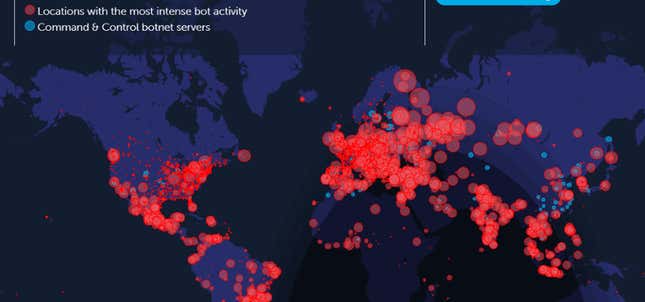
Security professional here:
If your operating system isn’t still getting security updates, get the heck off it ASAP. With the vulnerabilities that are left behind for Windows XP and Windows 7, it’s about a coin flip if your computer is already part of a botnet that attackers are using to launch global attacks. That’s…

Can confirm that Maxtrax work well in most types of snow and some ice. My neighbors keep getting stuck in front of my house, so I can just slap them down in front of their tires.
Once they are up the hill, and to maintained roads, they manage, but the Maxtrax get a workout at least a few times a year just to clear…
If you use two-factor authentication via SMS or have services that verify your identity through text messages, and those other devices aren’t secured or are shared with others, please don’t do this. If they are secured, cool, but this is a very good way to get someone bypassing your security, resetting your password,…
Likely scenario: Bipartisan does not mean overwhelming. It means they’ve got at least one person on either side working on it. So, they have to lobby with their individual sides to drive support. When an organization threatens those that might vote with it with loss of support or repercussions (blue flu, endorsing…
Absolutely. However, chromakeying lets you go the full video route if you want. You could even go so far as to put another body (clothed or unclothed) in place rather easily.
I actually wonder if that was the purpose - to invite a harmless distraction.
But can you get it in a “growler” - (because UK slang for lady garden is already a common beer term)
Lots of variables there. But encouraging it for others based on that would literally be the definition of survivorship bias.
I get that scientifically proven not to work reliably for others doesn’t mean jack when your experience differs, but it could easily be a case of infertility (or many, many other things).
Anecdotally, because everyone I know using this method has 4 kids or more? Often unexpectedly so?
Charting out cycles is prone to significant user error, general misunderstandings, and human variance. It’s also still dependant on abstinence at least a portion of the month and most people don’t do well with that.

Homeopathy is a specific belief about water memory and the power of dilution to use something otherwise harmful, to be beneficial. It’s has nothing to do with home remedies, which you’re mixing into this.
Here’s a great primer on it by an excellent channel:


